This is an opinion editorial by Moustafa Amin, a technology leader with more than 20 years of professional experience across large organizations, service providers and telephone companies.
Bitcoin is undoubtedly the world’s newest form of money. Governed by no central authority and controlled by no one, it represents the financial rescue that the world is looking for. In my opinion, Bitcoin freedom can be extended to escape eavesdroppers that work relentlessly day and night to intercept, monitor or even control our online activities.
Traditional VPN
Today, if two endpoints want to talk privately to each other, they typically need to do so via a trusted, third-party intermediary. As an example, consider what happens if any two endpoints want to set up a virtual private network (VPN) tunnel between themselves to carry on a private conversation over the public internet. They need to first be able to find out about each other. This is the discovery part.
If the two endpoints can somehow find each other, they may still not be able to directly communicate — for example, if they have private IP addresses or are hidden behind broadband routers or gateways. This is the data communication part.
Additionally, if more than one device wishes to share the same VPN channel to talk to each other, then additional information needs to be exchanged between all VPN points.
The first two parts of this process entail using a third party to facilitate discovery and communication. For example, the two endpoints need to buy a service from a VPN service provider and specify that they wish to communicate. The service provider serves as a trusted intermediary to the two parties.
Challenges
This third party not only needs to be trusted, but also must be reliable. If it is compromised, then the privacy is gone. It also needs to be always online. If this third party was to go out of business, the two endpoints cannot communicate with each other.
One pressing issue that is present in this centralized VPN model is the need to propagate a shared key to the communicating entities that they use to encrypt and decrypt the traffic between them. This key exchange usually happens over a separate channel — an out-of-band channel (think: email, phone, text message, etc). This apparently lacks the desired privacy-prohibiting eavesdropping or unlawful interception of the shared key.
Also, it is not uncommon in some countries to restrict known VPN ports. It happened to me when I opted in for an annual subscription for a well-known VPN service. I found that my VPN client couldn’t connect to any VPN server worldwide. I opened a case with the provider and fortunately, they understood the situation and refunded my money.
Moreover, some banks or other traditional financial systems (credit cards or payment processors) can deny or restrict payments if one attempts to subscribe to known global VPN services.
Now, the question becomes: How do we allow two or more entities to communicate among themselves without the use of third-party intermediaries, thus avoiding all these issues? To answer this, I am glad to introduce Bitcoin VPN.
What Is Bitcoin VPN And How Does It Work?
Bitcoin VPN is a solution that leverages the Bitcoin network (Layer 1) or the Lightning Network (Layer 2) to allow two or more parties to discover each other and be able to communicate privately over the public internet.
As with traditional VPN, a Bitcoin VPN client needs to access the web portal of their desired VPN service. This client could be a telecommuter that needs to be connected and access their corporate headquarters, or a normal VPN user who wants to access the internet from another location to bypass some content restriction for example.
When they opt for the VPN service, the client will be presented with a Lightning invoice or simply a wallet address along with an equivalent transaction amount that needs to be sent. In the case of a telecommuter, the transaction amount should be minimal (no enterprise would bill their employees to connect to their network). For a regular VPN service, the transaction could be an hourly bill.
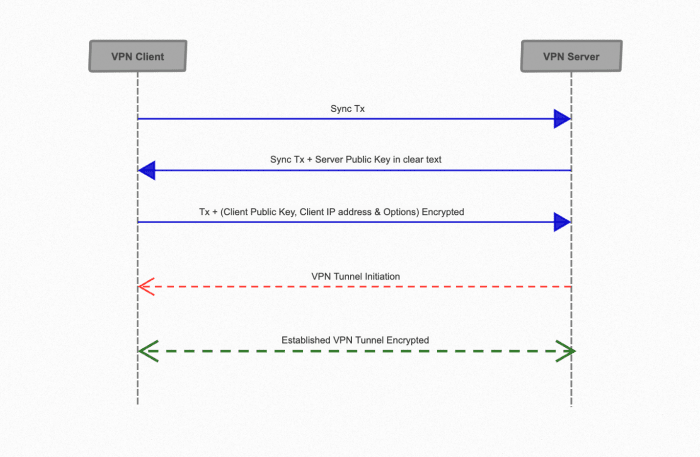
In all cases, the client sends the transaction to the presented Bitcoin address.
Once received, the VPN server responds by sending back to the client a transaction and passes the server public key as a clear text embedded in the transaction metadata.
As everything is publicly stored on the Bitcoin ledger and to avoid any possible eavesdropping, the client encrypts the following data using the received server public key:
- Client public IP address.
- Client public key.
- Other options that would be needed for the VPN connection (port number, etc.).
The client sends another transaction to the server, embedding the encrypted message from the previous step in the transaction metadata.
The server decrypts the encrypted message using its private key.
Equipped with all required information for the VPN, the server then establishes the required VPN tunnel to the client (public IP address: port number) and pairs by utilizing the client public key for the VPN encryption. Note how this differs from a traditional VPN where the client is usually the initiator of the tunnel.
For anyone who would argue that the same could be achieved with other cryptocurrencies, my goal with Bitcoin VPN is to avoid the centralized nature and subsequent challenges of traditional VPNs by leveraging the true and most decentralized ledger out there (Bitcoin). Just put aside your desire to control and/or make money by uselessly injecting your inferior altcoin of choice in the conversation.
Finally, it is apparent that Bitcoin, with its unique decentralized architecture, offers unlimited opportunities other than its apparent financial capabilities.
This is a guest post by Moustafa Amin. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc. or Bitcoin Magazine.
Credit: Source link






















 Bitcoin
Bitcoin  Ethereum
Ethereum  XRP
XRP  Tether
Tether  Solana
Solana  USDC
USDC  Dogecoin
Dogecoin  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  TRON
TRON  Wrapped Bitcoin
Wrapped Bitcoin  Wrapped stETH
Wrapped stETH  Chainlink
Chainlink  Avalanche
Avalanche  Sui
Sui  Stellar
Stellar  Litecoin
Litecoin  Toncoin
Toncoin  Shiba Inu
Shiba Inu  Hedera
Hedera  LEO Token
LEO Token  USDS
USDS  Hyperliquid
Hyperliquid  WETH
WETH  Polkadot
Polkadot  MANTRA
MANTRA  Bitcoin Cash
Bitcoin Cash  Bitget Token
Bitget Token  Ethena USDe
Ethena USDe  Wrapped eETH
Wrapped eETH  Uniswap
Uniswap  Monero
Monero  NEAR Protocol
NEAR Protocol  Pepe
Pepe  WhiteBIT Coin
WhiteBIT Coin  Aave
Aave  Ondo
Ondo  Bittensor
Bittensor  Aptos
Aptos  Internet Computer
Internet Computer  Dai
Dai  Official Trump
Official Trump  Mantle
Mantle  Ethereum Classic
Ethereum Classic  Tokenize Xchange
Tokenize Xchange  OKB
OKB  Gate
Gate  sUSDS
sUSDS  Coinbase Wrapped BTC
Coinbase Wrapped BTC 
