Research conducted by blockchain data platform Chainalysis estimated that $2 billion was lost from cross-chain bridge hacks so far in 2022.
Chainalysis stated in the report that the issue now “represents a significant threat to building trust in blockchain technology.”
Moreover, researchers said bridge hacks are favored by North Korean hackers, who are estimated to account for half of the $2 billion stolen to date.
The report comes hot on the heels of the Nomad bridge hack, in which $191 million was stolen. Nomad links the Ethereum, Avalanche, Evmos, Moonbeam, and Milkomeda blockchains.
Cross-chain bridges have multiple points of vulnerability
Cross-chain bridges connect different blockchains, enabling the transfer of data or tokens between otherwise incompatible chains. The technology is part of a drive to make the entire crypto ecosystem interoperable.
Bridges make it possible to use assets on a different blockchain without going off-chain to trade for the required token on an exchange. Typically, they operate by an asset conversion process using a lock-mint-burn mechanism.
However, bridges are susceptible to several vulnerabilities, including a single point of failure/centralization, low liquidity as the centralized entity must keep a pool of assets, technical vulnerabilities as the lock-mint-burn mechanism is governed by smart contracts, and censorship.
Chainalysis recommendations
The Chainalysis report said 13 separate bridge hacks have occurred to date this year, representing 69% of all stolen funds.
Researchers charted a breakdown of other hacks versus bridge hacks showing no discernable pattern. Before Q3 2021, bridge hacks were non-existent. But Q1 2022 saw a peak in funds stolen from bridges; this coincided with a peak in total funds stolen.
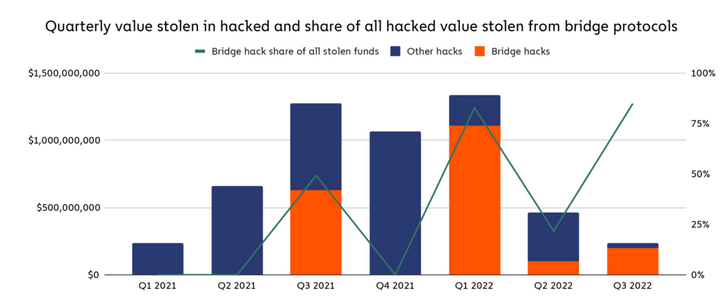
Chainalysis said in the report that, previously, exchanges were the primary target for hackers. But increased security at exchanges has forced hackers to seek out newer, more vulnerable targets to attack.
To counter the problem, researchers called for rigorous smart contract code audits and for proven contracts to be used as a template for developers to build on. Chainalysis also advised in the report on the “carelessness of human nature,” saying teams require training to spot “sophisticated social engineering tactics.”
Although not mentioned by name in the report, the above comment was in reference to the Ronin bridge hack, in which Axie Infinity users lost $615 million – the platform later refunded this.
It recently emerged that the Ronin bridge hack was orchestrated by North Korean hackers targeting a senior engineer with a fake job. The process involved fake interviews culminating with a job offer sent via an infected file. Opening the file allowed hackers to assume control of several network nodes.
Credit: Source link





















 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  Solana
Solana  XRP
XRP  Dogecoin
Dogecoin  USDC
USDC  Lido Staked Ether
Lido Staked Ether  Cardano
Cardano  TRON
TRON  Avalanche
Avalanche  Shiba Inu
Shiba Inu  Wrapped stETH
Wrapped stETH  Wrapped Bitcoin
Wrapped Bitcoin  Toncoin
Toncoin  Sui
Sui  WETH
WETH  Bitcoin Cash
Bitcoin Cash  Chainlink
Chainlink  Pepe
Pepe  Polkadot
Polkadot  LEO Token
LEO Token  Stellar
Stellar  NEAR Protocol
NEAR Protocol  Litecoin
Litecoin  Aptos
Aptos  Wrapped eETH
Wrapped eETH  Uniswap
Uniswap  USDS
USDS  Cronos
Cronos  Hedera
Hedera  Internet Computer
Internet Computer  Ethereum Classic
Ethereum Classic  Bonk
Bonk  Bittensor
Bittensor  Render
Render  Ethena USDe
Ethena USDe  POL (ex-MATIC)
POL (ex-MATIC)  WhiteBIT Coin
WhiteBIT Coin  Dai
Dai  MANTRA
MANTRA  Artificial Superintelligence Alliance
Artificial Superintelligence Alliance  dogwifhat
dogwifhat  Arbitrum
Arbitrum  Monero
Monero  Stacks
Stacks  OKB
OKB  Filecoin
Filecoin 
